PB616556
There are many challenges facing today's organizations. With outsourcing and mobile workforces, physical network boundaries are disappearing, giving way to "borderless networks." An increased threat environment demands more effective protection for business infrastructure and valuable information assets. Regulatory and industry mandates also impose strict security requirements. To protect their networks and data, organizations must establish visibility and appropriate access control for all users, and must discover and monitor IP-enabled devices.
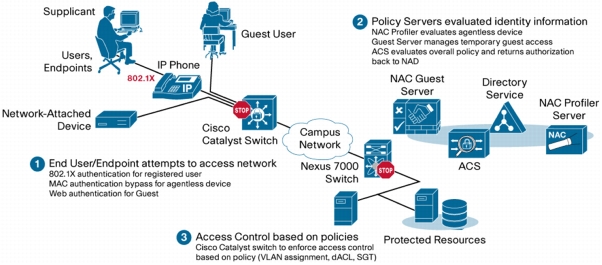
• Infrastructure: Cisco Catalyst® 2960, 2960S, 3560, 3560E, 3560X, 3750, 3750E, 3750X, 4500E, and 6500E Series Switches and Cisco Nexus® 7000 Series Switches interact with network users for authentication and authorization.
• Identity: Flexible authentication methods include 802.1X, web authentication, and MAC authentication bypass, all controlled in a single configuration for each switch port.
– Authorization and enforcement options: Besides VLAN and discretionary access control list (DACL) enforcement options, Cisco switches can tag each data packet with user identity information so that further controls can be deployed anywhere in the network. Accessing security groups using security group tags (SGTs) or security group access control lists (SGACLs) eliminates dependence on network topology, adding flexibility and significantly reducing traffic segmentation ACL management and overhead.
• Security services: Once users or devices are authenticated, additional security services can be applied to them. TrustSec integrates with Cisco NAC Guest Server for guest network access and with Cisco NAC Profiler for profiling and discovery of non-authenticating user devices, such as printers and IP phones. Data integrity via MACSec (802.1AE) address compliance by providing an encrypted link from the Catalyst 3750X or 3560X to the endpoint, or between data centers on the Nexus 7000.
• Client: TrustSec integrates with Cisco NAC Agent and the Cisco Secure Services Client (SSC). Cisco SSC provides 802.1X user and device authentication and manages user and device identity and network access protocols for secure wired and wireless access. Cisco NAC Agent is an optional lightweight agent running on an endpoint device. It performs deep inspection of the device's security profile by analyzing applications, registry settings, services, and files.
• Policy and management: In addition to handling the management of dynamic policies, Cisco Secure Access Control System (ACS) improves operations through its monitoring and troubleshooting features.
TrustSec Feature Highlights
• Flexible authentication: Cisco supports the most flexible authentication options in the market. Businesses can support multiple methods of authentication, including 802.1X for managed devices and users, web authentication for guests or non-802.1X users, and MAC authentication bypass for unmanaged or non-802.1X devices. Additionally, the order and priority of authentication methods can be configured, along with configurable behavior after 802.1X or AAA server failures.
• Flexible deployment modes: Cisco supports three deployment modes - monitor mode, low-impact mode, and high-security mode - providing a phased approach for 802.1X deployment. In particular, monitor mode enables 802.1X to be enabled but without enforcement; this allows businesses to monitor the network authentications, evaluate their risks, and prepare the network for access control in later phases.
• Multi-Domain Authentication Host Mode: Cisco supports secure 802.1X or MAC authentication bypass of the IP phone and of the PC behind an IP phone on the switch infrastructure. This allows authentication of an IP phone in the voice VLAN and multiple hosts on the data VLAN on each switch port.
• Unified guest access: Cisco offers guest access integration via the NAC Guest Server. This provides the same user experience for guest access, regardless of whether the connectivity is wired or wireless.
• Profiler: The ability to identify and profile non-authenticating devices in the network is an important component of a complete NAC architecture. TrustSec integrates with NAC Profiler to enable automatic endpoint discovery and real-time and historic visibility for all endpoints.
• Security group access: SGTs enable user traffic to be tagged with identity/role information once authenticated at the ingress of the network. This creates a flexible, scalable, role-based architecture that uses SGACLs to control this traffic deeper in the network. For businesses using legacy platforms, Cisco offers the Security Group Tag Exchange Protocol (SXP), which enables identity information to be propagated to an SGT-capable device.
• Monitoring and troubleshooting: Monitoring and troubleshooting features in Cisco Secure ACS 5.2 allow IT administrators to quickly debug and troubleshoot authentication and security group access features, from live authentication results and statistics of endpoints to SGACL views when policies are triggered.
Deployment Topology
Figure 1. TrustSec Deployment Topology - Campus/Branch Wired and Wireless
Platform Support Matrix
Cisco Services
For More Information